What is a SIM Swap Attack?
The FBI says SIM swap attacks are rising. Learn what this mobile-based attack is and how it is used to access victim accounts.
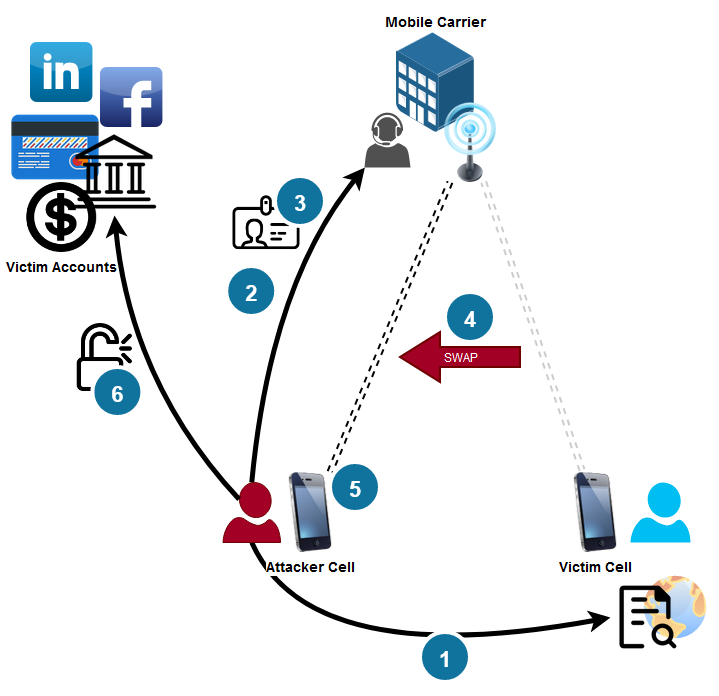
In February of last year, the FBI sent out a Public Service Announcement about the rising incidence of SIM swapping attacks. What is that you say? A SIM swap is a type of social engineering attack where a criminal convinces your mobile provider to transfer your account phone number to a different SIM card possessed by the criminal. Then, they do bad things with access to your phone number. For example this man lost his life savings. Let's dive in and learn what this attack looks like and some basic protections against it.
Here are the common steps in at least one method of SIM swap attack:
- Gather personal information about the victim, such as their full name, date of birth, address, and social security number. (Available on the dark web, exposed from data breaches and leaks)
- Contact the victim's mobile service provider and claim to have lost their SIM card or that it is damaged.
- Request that the service provider transfers the victim's phone number to a new SIM card in their possession.
- To complete the transfer, provide verification information, such as the victim's social security number or answers to security questions.
- Once the transfer is complete, the attacker can make and receive calls and texts via the victim's phone number.
- Use the victim's phone number to access their personal or work accounts, such as email, banking, and social media, which may rely on SMS-based two-factor authentication for access or password reset. Use this access to stage additional attacks.
Several sources noted this attack often takes place via insider threat and not always an external threat.
In their announcement, the FBI provides more details on what happens after the SIM swap is successful. They said:
"Once the SIM is swapped, the victim's calls, texts, and other data are diverted to the criminal's device. This access allows criminals to send 'Forgot Password' or 'Account Recovery' requests to the victim's email and other online accounts associated with the victim's mobile telephone number. Using SMS-based two-factor authentication, mobile application providers send a link or one-time passcode via text to the victim's number, now owned by the criminal, to access accounts. The criminal uses the codes to login and reset passwords, gaining control of online accounts associated with the victim's phone profile."
How Can You Protect Yourself?
A few highlights from my reading across analysis from different sources:
- Most of the security control responsibility is in the hands of our mobile providers. They are ultimately responsible for authenticating the transfer to a different SIM. This means you should research your provider and understand how they are protecting your account from fraudulent SIM transfer.
- Enable Multi-Factor Authentication everywhere possible. If your provider has neither MFA or an account PIN, then consider switching providers😬
- Avoid using SMS/text based multi-factor where possible on sensitive accounts. Instead use software or hardware tokens. See CISA recommendations for details.
- If you only have MFA on the account, be sure to ask if authentication is required on requests for SIM transfer. If it isn't then MFA is only helping to protect your online logon and not from the actual SIM swap attack.
- Ask about additional PIN or passwords to protect account changes, you should enable them.
- Avoiding the proliferation of your personal and sensitive information on the web helps to stop threat actors from having everything they need to spoof your identity. This is tough with the number of sites, portals and apps we use and the poor cybersecurity posture of most entities that have our sensitive data.
BleepingComputer shared some tips from the FTC and FBI on protecting yourself from a SIM swap attack.
Other Reading and Resources
Hackers Claim They Breached T-Mobile More Than 100 Times in 2022. Krebs has a fascinating write-up on SIM-swapping in relation to cybercrime, T-Mobile, and other entities.
I found a new cellular provider marketing primarily on security. Efani - The founder was attacked via SIM swap a few times and got tired of it. I don't know anyone using this company, and it looks expensive, marketed towards VIPs, but I think it is interesting how an entire mobile provider rose out of a market opportunity created by the impact of this threat.
Rob Ross lost life savings due to SIM Swap attack
Regional Enforcement Allied Computer Team is fighting SIM swapper criminals many of which conduct cryptocurrency theft post-SIM swap.
